Two fake soccer websites helped the creators of the Stuxnet computer virus that last year attacked computers used in Iran’s nuclear program mislead authorities as they launched their assault as part of a covert campaign involving assassinations of nuclear scientists and mysterious blasts at Iranian nuclear and military facilities.
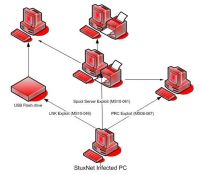 |
| Source: KrebsOnSecurity.com Click to enlarge |
The creators used the websites, www.mypremierfutbol.com and www.todaysfutbol.com, as fronts to communicate with Stuxnet-infected Iranian computers in a bid to make Iranian authorities believe that related traffic originated with soccer fans, according to a Reuters news agency story.
The story discloses details of how Stuxnet was developed and deployed based on research conducted by cyber warfare expert John Bumgarner, a retired U.S. Army special-operations veteran and former intelligence officer, who is chief technology officer of the US Cyber Consequences Unit, a non-profit group that studies the impact of cyber threats.
The Stuxnet virus created havoc in computers that control Iranian centrifuges designed to enrich uranium in the Islamic republic’s underground Nantaz nuclear facility and is believed to have set the program back by several months. It reportedly affected 1,000 of Iran’s estimated 8,000 centrifuges.
In a second cyber war incident, Iran said last month that it had discovered traces of the Duqu virus on which Stuxnet was based but had developed software to stop it before it created damage. Security software company Symantec Corp said in October that it had noticed a virus with a code similar to that of Stuxnet. Unlike Stuxnet, which is designed to take out control systems, Duqu is intended to collect data in advance of a cyber-attack.
Stuxnet is widely believed to have been developed by Israel and the United States as part of a covert effort to prevent Iran from acquiring the capability to build nuclear weapons. An enhanced upgraded version of the virus is reported to be close to completion.
It is difficult to see the virus attack on the Iranian computers independent of the assassination of at least three key Iranian nuclear scientists in the past two years as well as a series of explosions in Iran.
A blast last month at the Bid Ganeh Revolutionary Guards base 48 kilometers west of Tehran killed 17 people, including General Hassan Tehrani Moghaddam, a key figure in the Islamic republic’s missile development program. Iran’s assertion that the explosion was an accident has widely been greeted with scepticism. Iranian officials acknowledged that the explosion happened as scientists were working on weapons that could be used in an attack on Israel.
Iranian officials however denied that a second blast in Isfahan days after the Bid Ganeh incident involved a nuclear facility in the city where raw uranium is believed to be converted to uranium hexafluoride, the gas used in centrifuges in the initial phase of the process to enrich yellow cake.
The officials initially said the blast was related to a military exercise but later denied that any explosion had occurred. At least two more unconfirmed explosions are reported to have happened at facilities that host Iranian Shahab‑3 medium-range missiles capable of carrying nuclear warheads.
Two Iranian nuclear scientists, Fereydoon Abbasi-Davan and Majid Shahriari, were targeted in bombings in Tehran late last year in separate attacks. Mr. Abbasi-Davan survived the attack and was subsequently appointed as head of Iran’s Atomic Energy Organization while Mr. Shahriari was killed. The modus operandi in both attacks was the same: a motorcyclist who attached a bomb to the vehicles that they were travelling in.
In related incidents, nuclear scientist Darioush Rezaie was killed in Tehran by gunmen in Tehran in July of last year while Massoud Ali Mohammadi died in a bombing in the Iranian capital in January 2010. A Tehran court convicted in August Majid Jamali Fashi to death on charges of having been involved in the murder of Mr. Mohammedi on behalf of Israel’s Mossad intelligence agency.
The incidents are believed to be part of a covert campaign designed to complement ever tougher sanctions imposed on Iran and make a military strike against Iranian nuclear targets less likely.
Cyber warfare expert Mr. Bumgarner told Reuters that the fake soccer websites were part of a far larger effort to create a smoke screen behind which the Stuxnet virus attack could be launched undetected. Mr. Bumgarner said that an earlier virus, Conficker, that infected millions of computers in 2008 and was still dormant in many of those computers across the globe enabled the creators of Stuxnet to launch another attack with an improved version of the virus whenever they were ready.
While such an attack is likely, it is less likely to employ soccer as a deception.
About The Author:
James M. Dorsey is a senior fellow at the S. Rajaratnam School of International Studies at Nanyang Technological University in Singapore and the author of the blog, The Turbulent World of Middle East Soccer.

 von
von 